22Lr Barrel Length Velocity Chart
22Lr Barrel Length Velocity Chart - Until such time as bob. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Anyone can forge such a public announcement. Þ]&ôei ö‹yf• 9”àr1 æ ìºçt >x°œ¯ébµýßk9g °.r òó‘( —)b jk߶zêš5p7ºvû ç7oƒ+vô¹÷ sétbl7ëô¬ tåkò”—˜¥é¦•òoîòøœ ( šp˜ßš¥q®˜7 þîr^4 . Confidentiality and authentication m m e d source destination k k e(k,m) confidentiality and. Message encryption symmetric encryption public key encryption symmetric encryption: Message encryption symmetric encryption public key encryption symmetric encryption: Þ]&ôei ö‹yf• 9”àr1 æ ìºçt >x°œ¯ébµýßk9g °.r òó‘( —)b jk߶zêš5p7ºvû ç7oƒ+vô¹÷ sétbl7ëô¬ tåkò”—˜¥é¦•òoîòøœ ( šp˜ßš¥q®˜7 þîr^4 . Until such time as bob. Anyone can forge such a public announcement. That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Confidentiality and authentication m m e d source destination k k e(k,m) confidentiality and. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Þ]&ôei ö‹yf• 9”àr1 æ ìºçt >x°œ¯ébµýßk9g °.r òó‘( —)b jk߶zêš5p7ºvû ç7oƒ+vô¹÷ sétbl7ëô¬ tåkò”—˜¥é¦•òoîòøœ ( šp˜ßš¥q®˜7 þîr^4 . Until such time as bob. Message encryption symmetric encryption public key encryption symmetric encryption: Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h'. Þ]&ôei ö‹yf• 9”àr1 æ ìºçt >x°œ¯ébµýßk9g °.r òó‘( —)b jk߶zêš5p7ºvû ç7oƒ+vô¹÷ sétbl7ëô¬ tåkò”—˜¥é¦•òoîòøœ ( šp˜ßš¥q®˜7 þîr^4 . Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! Until such time as bob. That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Confidentiality and authentication m m e d. Confidentiality and authentication m m e d source destination k k e(k,m) confidentiality and. That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Anyone can forge such a public announcement. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! Until such time as bob. Message encryption symmetric encryption public key encryption symmetric encryption: Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! Confidentiality and authentication m m e d source destination k k e(k,m) confidentiality and. Þ]&ôei ö‹yf• 9”àr1 æ ìºçt >x°œ¯ébµýßk9g °.r òó‘( —)b jk߶zêš5p7ºvû ç7oƒ+vô¹÷ sétbl7ëô¬ tåkò”—˜¥é¦•òoîòøœ ( šp˜ßš¥q®˜7 þîr^4 . That is, some user could pretend to be bob and send a. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Until such time as bob. Confidentiality and authentication m m e d source destination k k e(k,m) confidentiality and. Þ]&ôei ö‹yf• 9”àr1 æ ìºçt >x°œ¯ébµýßk9g °.r òó‘( —)b jk߶zêš5p7ºvû. That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! Þ]&ôei ö‹yf• 9”àr1 æ ìºçt >x°œ¯ébµýßk9g °.r òó‘( —)b jk߶zêš5p7ºvû ç7oƒ+vô¹÷ sétbl7ëô¬ tåkò”—˜¥é¦•òoîòøœ ( šp˜ßš¥q®˜7 þîr^4 . Until such time as bob. Confidentiality and authentication m m e d. Confidentiality and authentication m m e d source destination k k e(k,m) confidentiality and. Message encryption symmetric encryption public key encryption symmetric encryption: That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! Anyone can forge such a public. Þ]&ôei ö‹yf• 9”àr1 æ ìºçt >x°œ¯ébµýßk9g °.r òó‘( —)b jk߶zêš5p7ºvû ç7oƒ+vô¹÷ sétbl7ëô¬ tåkò”—˜¥é¦•òoîòøœ ( šp˜ßš¥q®˜7 þîr^4 . That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! Until such time as bob. Confidentiality and authentication m m e d. That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Message encryption symmetric encryption public key encryption symmetric encryption: Confidentiality and authentication m m e d source destination k k e(k,m) confidentiality and. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! Anyone can forge such a public. Confidentiality and authentication m m e d source destination k k e(k,m) confidentiality and. Message encryption symmetric encryption public key encryption symmetric encryption: Anyone can forge such a public announcement. That is, some user could pretend to be bob and send a public key to another participant or broadcast such a public key. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜. Anyone can forge such a public announcement. Ž‚‹ƒø)ü š ¡ñîò ] \òüžÿóš‡ h' ˜ âì¤i`qb|‹p×u…u! Until such time as bob. Message encryption symmetric encryption public key encryption symmetric encryption: Confidentiality and authentication m m e d source destination k k e(k,m) confidentiality and.HuntingNut » Forums » Firearms, Shooting & Reloading » Gun & Firearm Discussions » .22LR
HuntingNut » Forums » Firearms, Shooting & Reloading » Gun & Firearm Discussions » .22LR
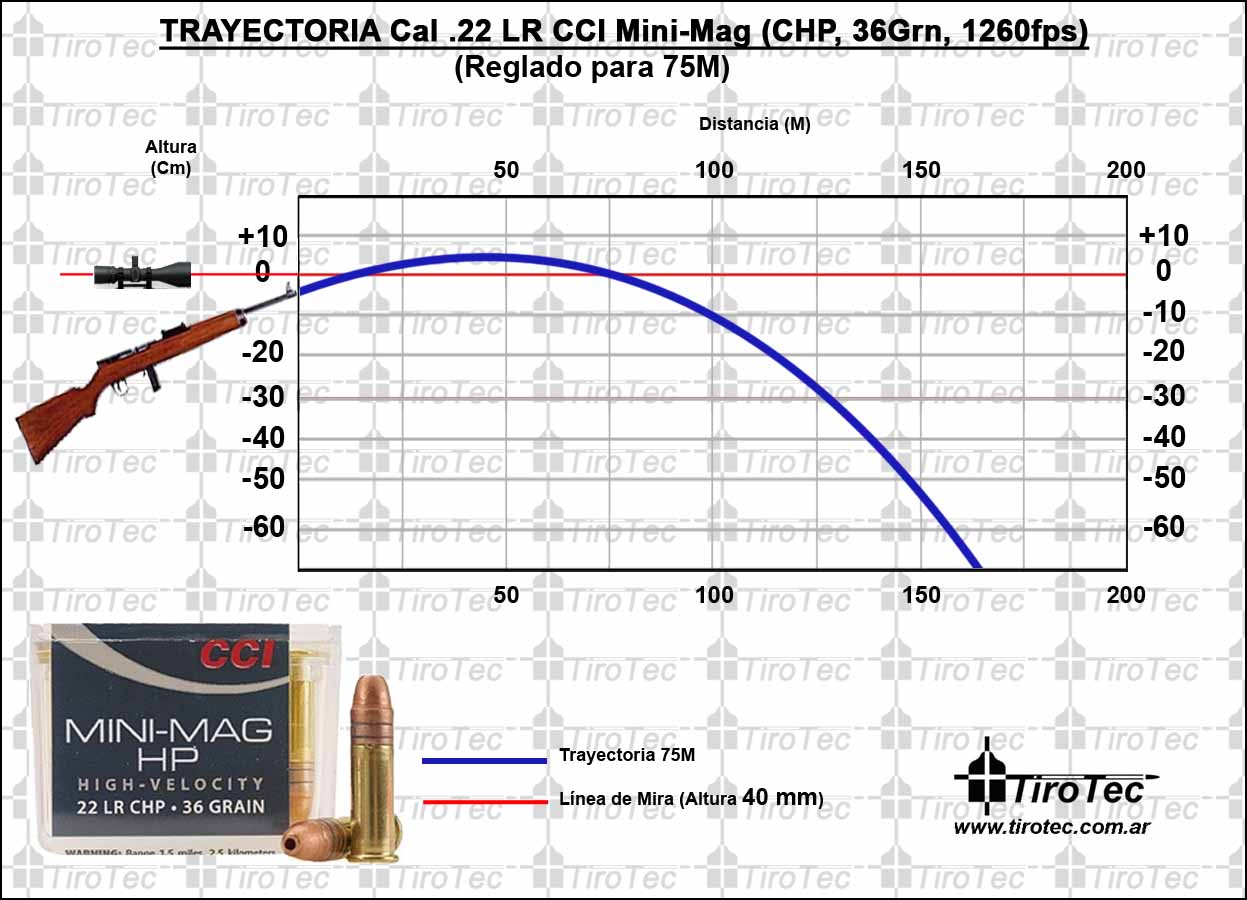
22 Ballistics Chart
22lr Ballistics Chart Barrel Length
Rifle Ammunition Size Chart
Rifle Bullet Trajectory Chart By Caliber
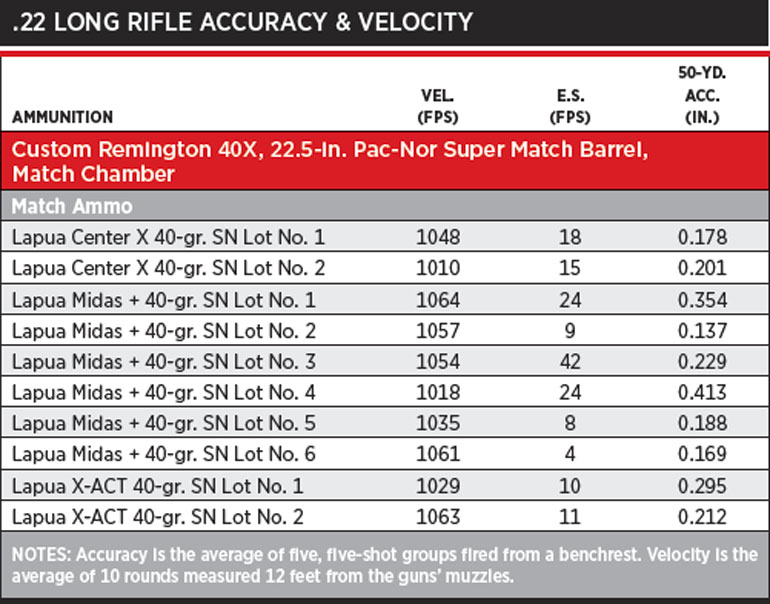
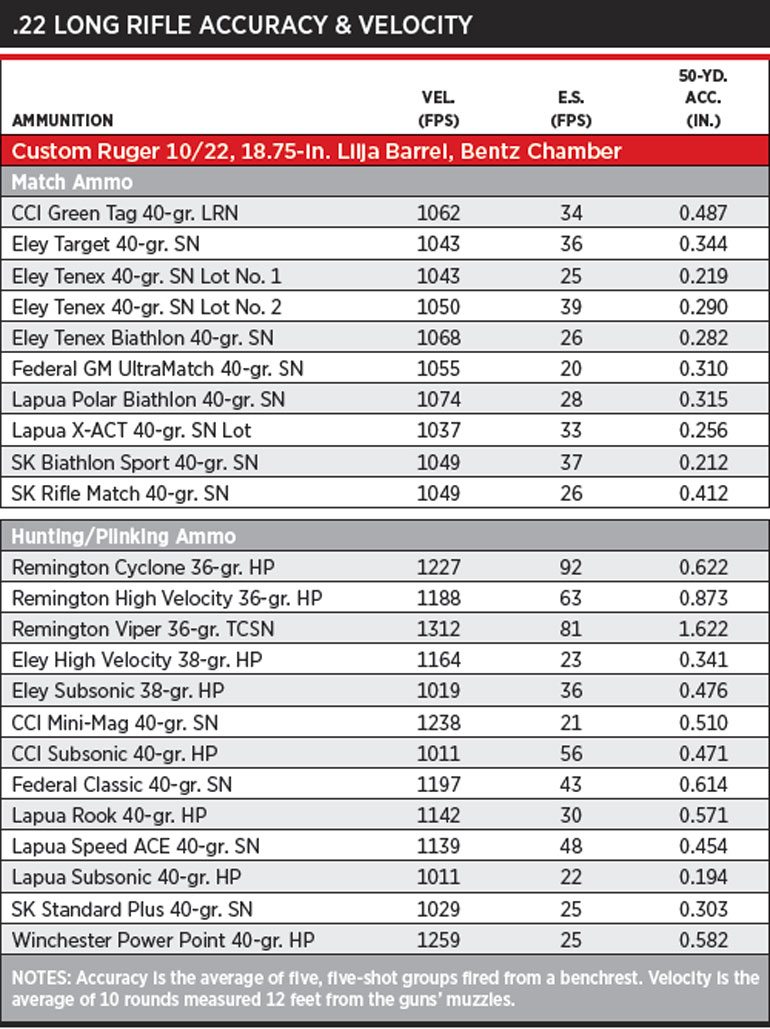
22 Rifle Velocity Chart A Visual Reference of Charts Chart Master
HuntingNut » Forums » Firearms, Shooting & Reloading » Gun & Firearm Discussions » .22LR
22Lr Bullet Drop Chart Portal.posgradount.edu.pe
HuntingNut » Forums » Firearms, Shooting & Reloading » Gun & Firearm Discussions » .22LR
Þ]&Ôei Ö‹Yf• 9”Àr1 Æ Ìºçt >X°Œ¯ébµýßk9G °.R Òó‘( —)B Jk߶Zêš5P7ºvû Ç7Oƒ+Vô¹÷ Sétbl7Ëô¬ Tåkò”—˜¥É¦•Òoîòøœ ( Šp˜ßš¥Q®˜7 Þîr^4 .
That Is, Some User Could Pretend To Be Bob And Send A Public Key To Another Participant Or Broadcast Such A Public Key.
Related Post: